Packer:
absent
Compilation date:
05:38:03 23.10.2019
SHA1 hash:
27e8474286382ff8e2de2c49398179f11936c3c5 (TosBtKbdLayer.dll)
Description
BackDoor.Siggen2.3243 is a malicious DLL module written in C++ and designed for 32-bit and 64-bit Microsoft Windows operating systems. Its functionality includes a keylogger, snooping on clipboard contents, extracting saved logins and passwords, obtaining information about installed applications and collecting general information about the infected system.
Operating routine
BackDoor.Siggen2.3243 is statically linked with several libraries, such as OpenSSL, SQLite, gloox XMPP client library, CJsonObject JSON parser and STL.
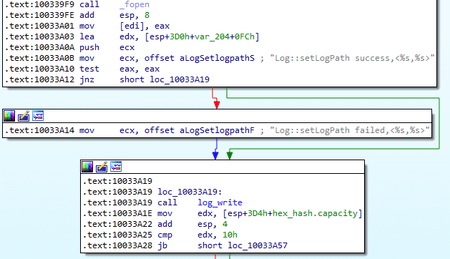
The trojan is loaded into the memory by BackDoor.ShadowPad.4 through the LoadLibrary function. At the beginning, it creates the [Guid("71ED330D-F80C-499A-A442-744EAD224A8F")] mutex. Next, in the current directory it creates a log file whose name is calculated as an MD5 hash of the winhook-clientLog string, which is eb3816e69e6c007b96a09e2ecee968e5. After that, the trojan writes the strings in this file as follows:
Info [YYYY-MM-DD HH:MM:SS]Log::setLogPath success,
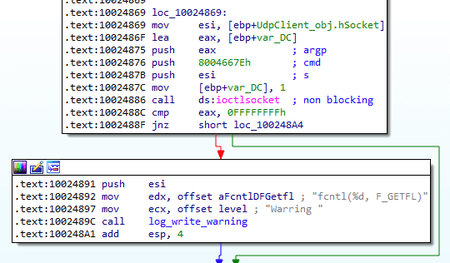
Info [YYYY-MM-DD HH:MM:SS]..Start.. 0.0.9a When running, BackDoor.Siggen2.3243 saves the information about every operation it performs, including information about the errors:
With that, the error messages are written with the Warring type. The example of such record is shown below:
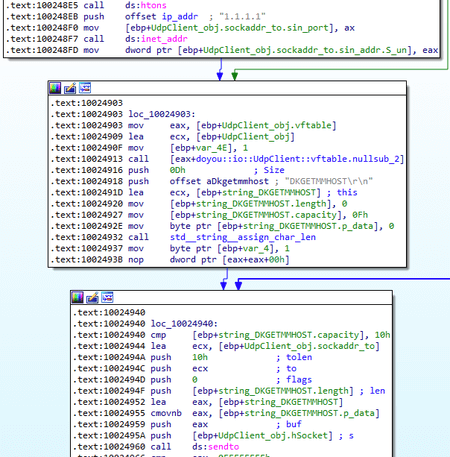
Using the UDP protocol, the trojan sends messages in the form of the DKGETMMHOST\r\n string to the remote server 1.1.1.1:8005, which belongs to the Cloudflare DNS service:
Sending such non-standard messages doesn’t have any practical use and can indicate the analyzed sample represents a test version of the trojan, and the 1.1.1.1 server address is used as a temporary plug.
In the response message from the server, BackDoor.Siggen2.3243 searches for the DKMMHOST:, followed by the address of the C&C server the trojan needs to connect to. In addition, in the current directory the backdoor searches for the file whose name is the MD5 hash of the register.json string. This file should represent a JSON configuration file encoded with Base64 and containing the parameters needed to connect to the C&C server.
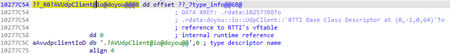
To communicate with the C&C server, the trojan uses JSON as well. BackDoor.Siggen2.3243 has the corresponding classes to establish the connection:
Artifacts
The malicious library contains the information about the path to the project file:
C:\Users\Administrator\Desktop\Fun\bin\Win32\Release\winsafe.pdb
The following strings can also be found in its body:
BrowseHistory.db
select url, title, last_visit_time, visit_count from urls
title
last_visit_time
visit_count
BrowseHistory::urlChrome, %s, %s
select id, title, last, hit from UserRankUrl
BrowseHistory::urlSogouExplorer,%s, %s
es.sqlite
select url, title, last_visit_date, visit_count from moz_places
last_visit_date
BrowseHistory::urlSogouExplorer, %s
\\2345Explorer\\User Data\\Default\\History
2345Explorer.exe
\\google\\chrome\\User Data\\default\\History
chrome.exe
\\360Chrome\\chrome\\User Data\\default\\History
360chrome.exe
\\User Data\\default\\History
\\360se6\\User Data\\default\\History
360se.exe
\\Tencent\\QQBrowser\\User Data\\Default\\History
QQBrowser.exe
\\SogouExplorer\\HistoryUrl3.db
SogouExplorer.exe
\\Mozilla\\Firefox\\Profiles
firefox.exe
++ %p s_buff_size = %u mb
-- %p s_buff_size = %u mb
write2socket1:sockfd<%d> client socket closed.
write2socket1:sockfd<%d> nSize<%d> nLast<%d> ret<%d>
sockfd<%d> onClose
warning, initSocket close old socket<%d>...
create socket failed...
<socket=%d> connect <%s:%d> failed...
hostname2ip(hostname is null ptr).
hostname2ip(port is null ptr).
%s getaddrinfo
%s getnameinfo
--\r\n\r\n
Content-Disposition: form-data; name=\"%s\"\r\n\r\n
!_form_data_buf.canWrite(bytesize), url=%s
readsize != bytesize, url=%s
readsize >= 1MB
Content-Disposition: form-data; name=\"%s\"; filename=\"%s\"\r\n
Content-Type: application/octet-stream\r\n\r\n
total %.2f GB (%.2f GB available)
system_hide::CreatePipe
system_hide::CreateProcess
wmic path win32_physicalmedia get SerialNumber
WMIC diskdrive get Name, Manufacturer, Model
LocalData::task_load::PathFileExists, %s
LocalData::task_load::read.data.empty, %s
LocalData::task_load::CJsonObject.Parse.empty, %s
LocalData::task_add::taskid exists %d
task_cache_init
LocalData::task_cache_init::taskids.IsEmpty()
LocalData::task_cache_init::read.data.empty, taskid=%s
LocalData::task_cache_init::Parse.data.empty, taskid=%s
LocalData::task_cache_init::task_state.empty, taskid=%s
cmd_10050
clipboard_records
cmd_10026
keyboard_records
set_do_scanfs_lasttime
/windows/register failed!
success
register failed!
register c2s!
application/json
Content-Type
/windows/register
token-refresh lost! to register_dev
token-refresh s2c <%d><%s>
token-refresh success! to start pushclient, token=%s
token-refresh failed! to register_dev
token-refresh c2s <%s>
/windows/token-refresh
submit-data warring! e.cmd<%s> != cmd<%s>
submit-data failed! <%s>
submit_data s2c <%s><%s>
submit_data s2c <%s><%d>
submit_data c2s <%p : %p> <%s>
/windows/submit-data
submit-file failed! <%s>
submit_file s2c <%s><%s><%s>
----boundaryb1zYhTI38xpQxBK00
multipart/form-data; boundary=
upfile
submit_file c2s <%p : %p> <%s><%s>
/windows/submit-file
endFile %s cbFun
remove %s
endFile %s
cmd_99998
message
do cmd_10001
mem_size
sd_sn
sd_model
sd_volume
sd_partitioning
volume
disk_size
file_sys
paration_table
remaining_percent
remaining_size
mac_net
mac_wifi
network
sd_info
camera
microphone
2.0.1
mm_version
cmd_10001
do cmd_10002
cmd_10002
appinfo
GetSoftInfo info.empty()
appname
version
install_time
install_path
uninstall_path
publisher
do cmd_10014
cmd_10014
all_request
GetBrowsHistory info.empty()
do cmd_10052
cmd_10052
browser_accounts
UserAccHistory info.empty()
{\"local_task\":\"true\",\"data\":{\"instructions\":{\"cmd\":\"cmd_10018\"}}}
do cmd_10013_log
2ecee968e5\", \"filename\" : \"eb3816e69e6c007b96a09e2ecee968e5\"}, \"extend\" : {\"id\":\"3f056c333f4f7ce015ec02f109454c54\", \"log_id\" : 2113}}}}
{\"code\":\"policypush\", \"data\" : {\"type\":\"policypush\", \"createdatetime\" : \"2019 - 07 - 17 15:51 : 00\", \"instructions\" : {\"cmd\":\"cmd_10013\", \"data\" : {\"path\":\"